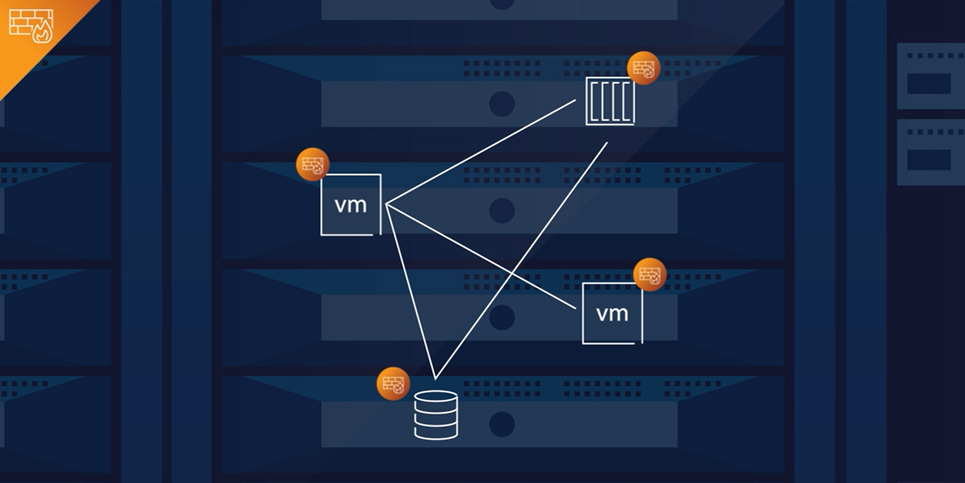
Complete East-West Security for Zero Trust

Deep Visibility and Granular Control
Gain visibility across all network flows to easily achieve granular micro-segmentation and generate context-aware policies for each workload.

Lateral Threat Detection and Prevention
Reduce the attack surface and defend against known and unknown threats moving within and across clouds with a modern, distributed firewall solution that is purpose-built to secure multi-cloud traffic across virtualized workloads.

Application Agility with Security
Unlock business agility by ensuring that workloads maintain their security policies throughout their lifecycle, regardless of where the workload lives or moves. Write policy once and automatically enforce everywhere.

Use the Right Firewall for the Right Type of Traffic
Organizations can no longer rely on edge firewalls alone. Internal firewalls are purpose-built to secure east-west traffic, providing defense-in-depth against threats that make it past the network perimeter.
Key Capabilities
Distributed Architecture
Get complete network security coverage across all flows with a stateful layer 7 firewall built-into the hypervisor and distributed at every workload.
No Network Changes
Radically simplify firewall deployment and operations without changing your network — no traffic hair-pinning required.
Elastic Throughput
Automatically scale with your workloads for massive traffic inspection capacity, eliminating the throughput constraints typical of appliance-based firewalls.
Superior Workload Context
Enjoy in-depth workload and network context from a unique position in the hypervisor. Achieve superior threat detection and faster forensics while remaining isolated from the attack surface.
Scalable Traffic-Flow Analysis
Get visualization, analysis and monitoring of all traffic flows for complex modern apps and large networks to enable micro-segmentation at scale.
Advanced Threat Prevention
Leverage signature and behavior-based detection engines to quickly identify and block known threats and new, evolving threats that have never been seen before.
VMware Cross-Cloud Services
Enable lateral security for your multi-cloud environment with NSX Distributed Firewall, a Networking and Security solution of VMware's Cross-Cloud services portfolio.
Address Critical Security Use Cases

Get Real-Time Visibility and Analytics at Scale
Get real-time visibility into applications and their security posture when you visualize workloads and traffic flows with contextual application topology maps. Quickly identify security gaps and get granular policy recommendations for segmentation.

Rapidly Deploy Network Segments
Easily create network segments by defining them entirely in software and avoid the need to re-architect your network or deploy discrete appliances.

Operationalize Zero Trust with Micro-Segmentation
Micro-segment all applications to achieve zero trust. Reduce the attack surface and isolate applications with granular segmentation policies that enable user- and application-specific access controls and mitigate lateral movement.

Ubiquitous Virtual Patching
Monitor traffic flows at every host and identify malicious traffic on a per hop basis with IDS/IPS. Then, apply virtual patching so that unpatched servers inside the data center are not exploited.

Rapidly Respond to Ransomware and Advanced Threats
Combine multiple detection engines including IDS/IPS, NTA, and Network Sandboxing to quickly identify and block threats from moving laterally across your network, even across encrypted traffic. Correlate security events across all detection engines with network detection and response (NDR) to help you prioritize and rapidly respond to threats.

Get Real-Time Visibility and Analytics at Scale
Get real-time visibility into applications and their security posture when you visualize workloads and traffic flows with contextual application topology maps. Quickly identify security gaps and get granular policy recommendations for segmentation.

Rapidly Deploy Network Segments
Easily create network segments by defining them entirely in software and avoid the need to re-architect your network or deploy discrete appliances.

Operationalize Zero Trust with Micro-Segmentation
Micro-segment all applications to achieve zero trust. Reduce the attack surface and isolate applications with granular segmentation policies that enable user- and application-specific access controls and mitigate lateral movement.

Ubiquitous Virtual Patching
Monitor traffic flows at every host and identify malicious traffic on a per hop basis with IDS/IPS. Then, apply virtual patching so that unpatched servers inside the data center are not exploited.

Rapidly Respond to Ransomware and Advanced Threats
Combine multiple detection engines including IDS/IPS, NTA, and Network Sandboxing to quickly identify and block threats from moving laterally across your network, even across encrypted traffic. Correlate security events across all detection engines with network detection and response (NDR) to help you prioritize and rapidly respond to threats.
Case Studies

“The internal firewall and micro-segmentation capabilities of NSX Data Center enabled us to rapidly deliver on our CIO’s Zero Trust initiative.”
— Mark Fournier, Director of IT Infrastructure

“The inherent security on the NSX platform allows our developers and security experts to work together from the get-go, weaving cybersecurity into the very DNA of the network.”
— Scott Tivendale, Capability Lead

“NSX has simplified the ability for us to segment those servers off into their own environment ... without having to make vast hardware purchases and additional firewalls and technologies.”
— Ben Moore, Lead Systems Engineer
Learn, Evaluate, Implement
Resources
Explore technical documentation, reports, trial, communities and more.
VMware Security Blogs
Read up on the latest network security topics.
Partners
Use Partner Locator to quickly find a VMware partner near you.
FAQ
View common question and answers about NSX.
NSX Security Tech Zone
Get the latest technical resources on the VMware NSX Security portfolio.
Ready to Get Started?